Streamlining user permission management for admins
I redesigned the user experience for granting and managing privileges for internal users by introducing the role-based access control (RBAC) system to simplify the overall management of user permissions.
What does DevRev do?
Connects customer support and product management via omni-channel communication, to give real-time insights. It provides self-service tools that elevates support team's impact across the organization.
Role
Product Designer
Collaborators
1 PM, 5 Engineers
Year
2024
Why access management matters?
In B2B products, all users have a distinct role that defines their responsibilities. Subsequently, each role gets specific access to the features and data to complete their work. Access control enables organizations to safeguard critical data while streamlining operational workflows.
Think of access as a digital key that unlocks doors in the online world. It grants permission to enter specific areas, use certain features, or perform particular tasks. Thorough access management is essential for a system to function securely—providing each individual with the right level of access to perform their duties without risking data breaches.
Existing experience
Before the redesign, the groups formed for team management and operational purposes were used to grant privileges. The privileges were defined at a group level. Consequently, every group member received the same level of access, regardless of their specific roles and responsibilities. This method made it difficult for admins to manage individual privileges effectively.
Current flow for granting privileges via groups
Identifying the problems
Inflexible Access Tied to Group Membership: The access was granted to a group, so each group member got the same level of access. Changing a user's group for organizational purposes unintentionally affected their access. Also, there was no way to customize the access for individual users.
Limitation on configuration: Access could be granted only for actions such as Create, Read, Update, and Delete. Apart from these actions, many other configurations still needed to be included, and the current UI didn't support it.
Fragmented access configuration: There was no single view to configure the access for the users. It was fragmented and was controlled from various places in the app. This fragmentation mades obtaining a clear, holistic view of a user's overall privileges difficult.
I want a more effective way to manage groups with clearer definitions of the access granted to each team member.
I would like to have a display that shows more clearly which group/role the user is assigned to.
I need a better way to differentiate between privilege groups and ticket groups.
Few points from the customer feedback
Who are the users?
👩🏻🦱
Admins
Responsible for managing user access, assigning roles, and ensuring the right permissions are granted across the organization.
🧔🏻♂️
End users
These users request access to specific features, tools, or data based on their responsibilities. They depend on the system to provide timely permissions for them to perform their tasks efficiently.
Goals
The goal was to allow admins to regulate who can view, modify, or interact with different parts, features, and objects in the system from the interface. This will minimize the dependency on the backend engineers at DevRev for configuring each role.
Key factors to consider when assigning privileges include-
1. Who is the user?
2. What are their roles and responsibilities?
3. Which interfaces do they interact with?
Designing solutions to overcome challenges
I had numerous discussions with the team about various aspects of the project, from approaching the problem to laying the information architecture, planning features, and future-proofing. We had multiple brainstorming sessions to come up with solutions.
Brainstorming ideas on Figjam
Our guiding principles-
Our key was to ensure the admins are able to configure role with ease. We formulated design principles which were directed us through the process.
Strategies for solving the problem
Decoupling of groups and privileges
Groups were used for organizational and access control purposes, leading to inefficiencies, where all users in a group receive the same privileges. Hence, separating the aspects of managing access from the groups was essential.
Access can be controlled by assigning each individual a role. Therefore, an RBAC (role-based access control system) was the most relevant. By separating these functions, groups could continue serving operational needs while roles were introduced to handle permissions.
Assigning roles to individual users or segments
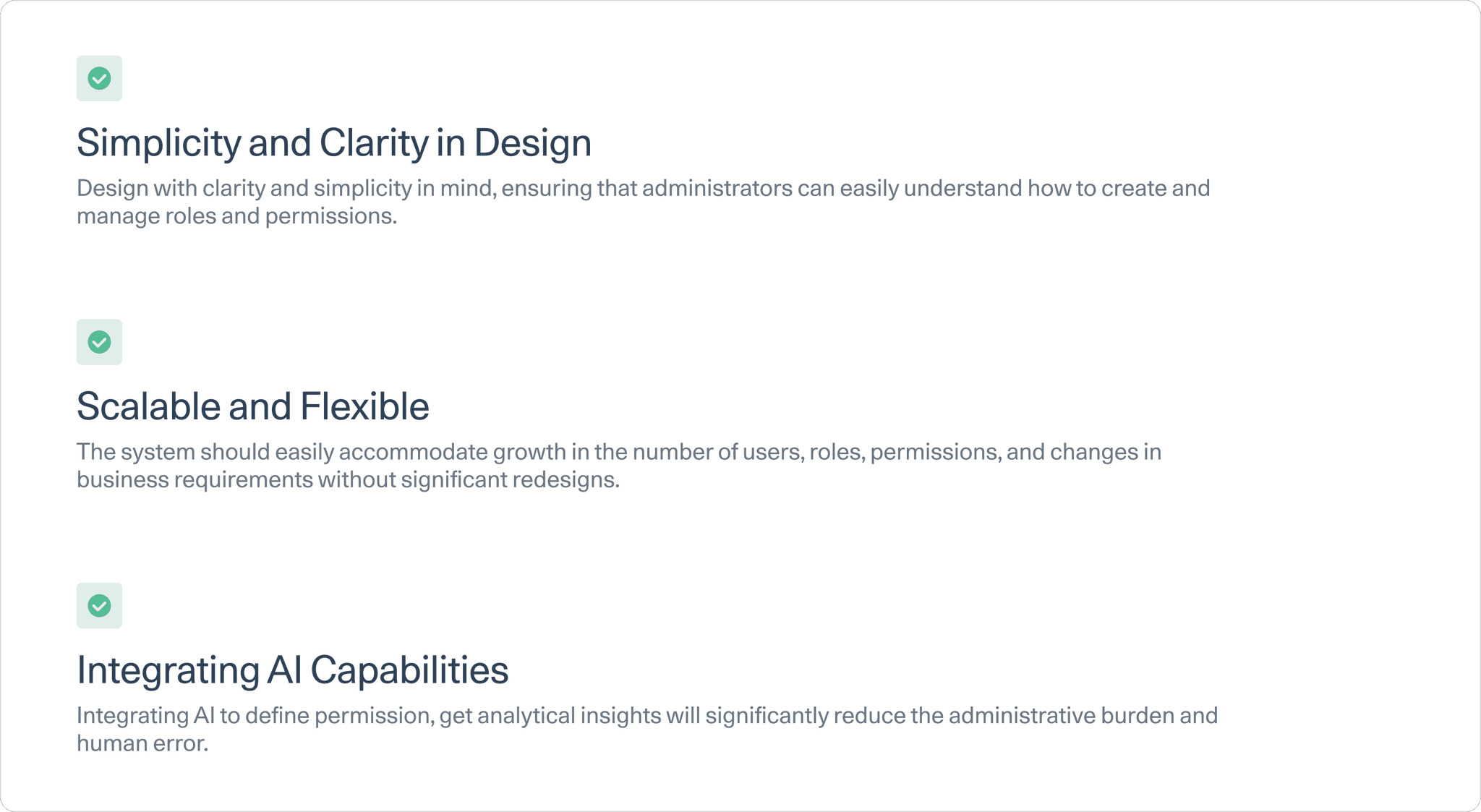
Categorisation for scalability
The designs had to be scalable to accommodate any new feature getting released. To keep the framework flexible and scalable, we created categories of the features and logically structured them. We began by listing all the objects and grouped them according to the user's persona. For instance, a support engineer would require access to customer tickets, SLA, and routing rules. So, these feature and objects were grouped together.
Centralised system powered by AI
The process of granting access is highly complicated and tedious. At the same time, it might lead to security-related issues if not done correctly. Hence, we planned to leverage AI to simplify the role creation and management process. With the help of prompts, the admins can easily create roles and assign them to the required users. Admins can also ask questions about any breach happend and the cause of it.
Final designs
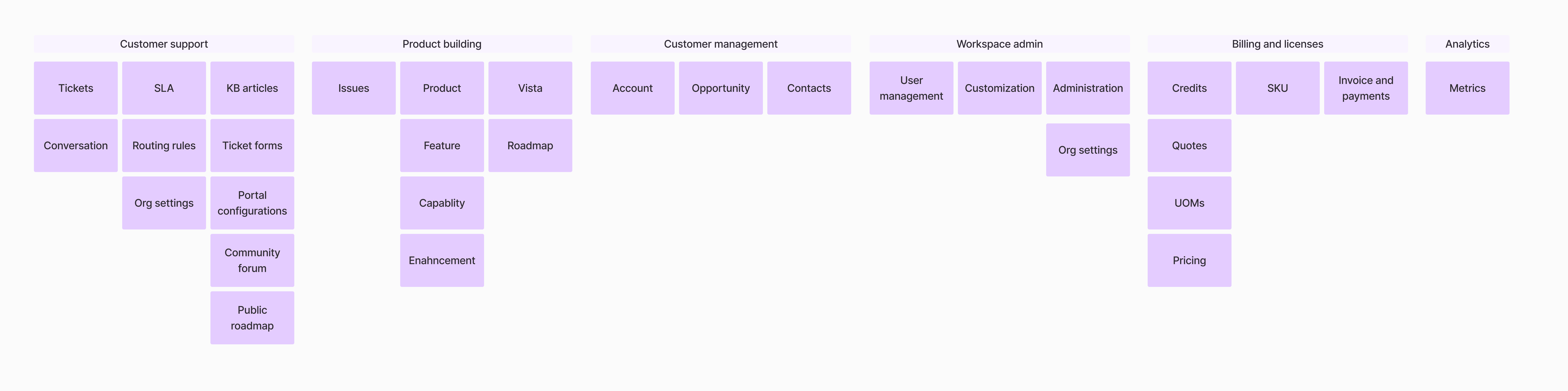
We created a roles dashboard with three tabs:
List of roles
This tab allows admins to create, manage, and assign roles to users or groups. It provides a streamlined way to view all existing roles and make adjustments as needed.
Managing access requests
Considering the change in responsibilities or assigned projects, a user might need additional access. So, the users can request the admins, and the admins can then review the requests in this tab. The admin can either accept or reject the requests.
Analytics (planned for next phase)
Analytics will focus on identifying potential issues within roles, assessing system performance, spotting security breaches, and detecting cases of over-privileged access. This will give admins valuable insights into role effectiveness and system security. Analytics combined with AI could give insights to improve the role resulting in better performance.
Creating a role
Creating a role from scratch requires significant effort, as the administrator must consider multiple elements. However, this process becomes easier with the use of AI. The administrator can describe the desired persona as a prompt, and AI can generate a suitable role for that persona. The administrator can then fine-tune the role to meet specific requirements.
Additionally, we interviewed existing customers to gain insights into commonly used roles. Based on this feedback, we curated a list of 10 templates that can be utilized, eliminating the need to create roles from the ground up.
Privilege sets
In the previous system, privileges were defined only with respect to actions like 'Create,' 'Read,' 'Update,' and 'Delete' objects or features. This was significantly problematic since object-specific privileges like 'Can comment,' 'Can link objects,' or 'Can create drafts,' and so on could not be configured, and the standard actions were not enough. Hence, according to each object and feature, I created a list of relevant privileges.
This will enable the admin to grant more specific permissions. We finalized the designs after multiple iterations for each set of privileges.
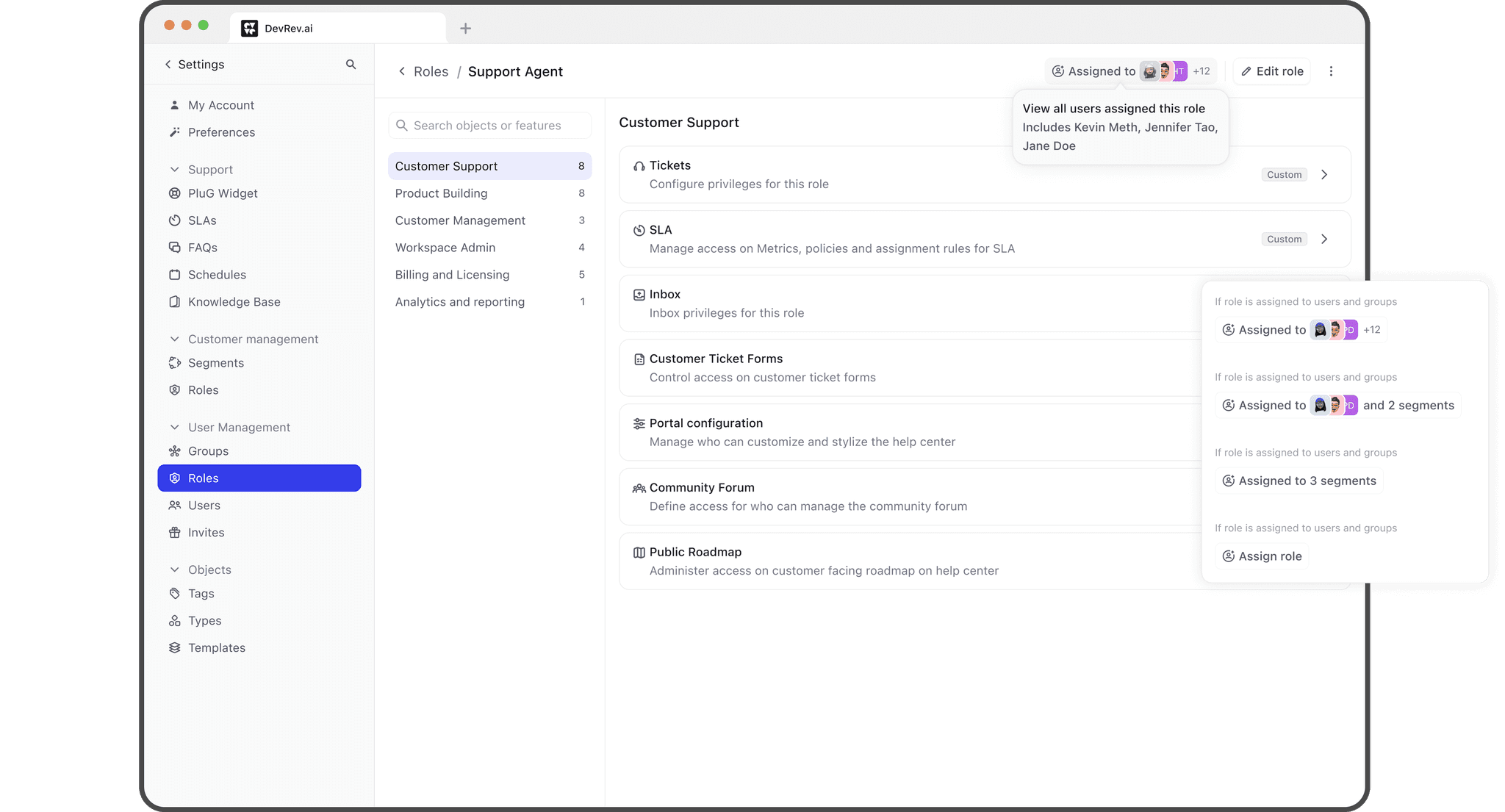
Assigning roles to individual users or segments
Adding conditions while granting privileges
Assigning roles to users
Role—a set of specific privileges is then assigned to individuals.
Assigning roles to individual users or segments
Granting additional privileges
In case of individuals who require additional privileges. Instead of adding this privilege to the entire role, an additional privilege can be assigned to the user.
Additional privileges on profile page
Insights from Turing
Admins can derive insights about the performance of the roles, and foresee any breaches or loops in the assignment with the help of AI. The admin must ask the query, and AI will check and generate answers.
Key takeaways-
Understanding complexity: I had to delve deeper into understanding the problem statement and the various use cases—without which I would not have come to a feasible solution.
Balancing simplicity with scalability: Regardless of the complexity of the problem, it is essential to maintain simplicity. The users can only utilize an intuitive interface. Simplicity will also allow for scalability, accommodating future requirements.
Collaboration is key: Throughout the process, I had numerous discussions with the product manager and engineers at each design stage. These discussions helped refine the ideas and uncover edge cases that would have been difficult to identify.